Why User Vigilance Is Important
Today we received a gentle reminder that no matter how hard we work to keep out cyber-threats, there is always a weak link to target in any business system. The users. This exploit concerns a VAT Return and Payment Overdue scam email which was received in the office today. The instant reaction was to jump to the conclusion that we had to do something quickly, to avoid a penalty. Which is just what the reprobate behind the email was hoping.
What To Look For
This is a warning about a VAT Return and Payment Overdue scam email, which may catch out the unwary. If you are a business owner or have responsibility for finance matters please watch out for this innocent looking communication.
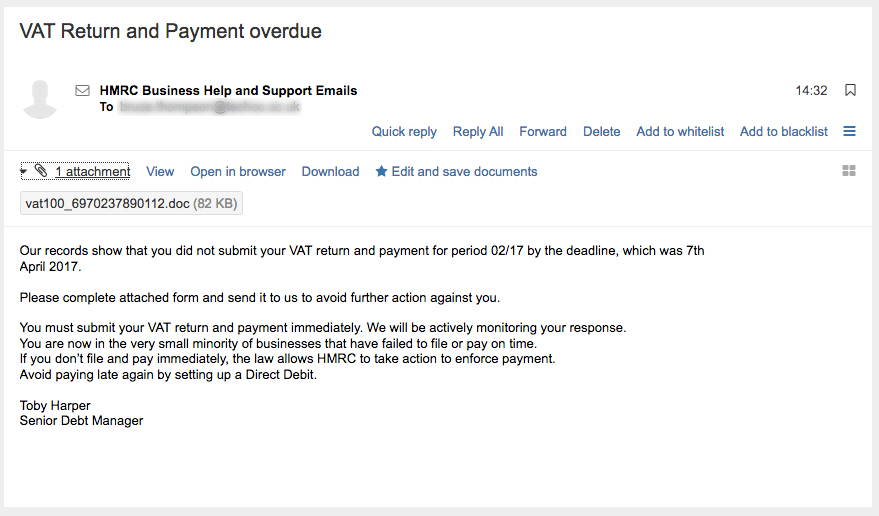
How To Tell It Is A Scam Email
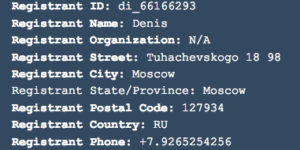
If you hover the mouse over the sender, most good email systems will tell you the address you will be replying to. In this case you will not be surprised to learn that it is not from HM Revenue and Customs (HMRC) at all! It comes from a suspicious email address which is registered to someone called Denis. Denis apparently lives in Moscow, and is using the unlikely email address of info@hmrccustomersupport157.top.
When The Penny Drops
After a few laps of the office, looking for a quick solution, or a way to pass responsibility over to someone else, the recipient had the good sense to check up via the HMRC website. The information there on the site , which is linked below, made him think twice. He reported the matter to Information Security, fortunately, before clicking on and opening the email attachment.
Cost of the VAT Return and Payment Overdue Scam
In our case, the cost of this particular email scam was trivial. It mostly involved additional wear and tear on the carpet and some lost productivity. According to an anonymous source in finance, there was also some lost paint from the ceiling. It could have been much more costly, if the user had opened the attachment and did not have up to date anti virus.
While HMRC may send you an email if you are overdue with VAT payments, they will use the normal contact email address, and will recommend that customers pay online to avoid further action. These emails will never ask you to provide personal or financial information. You won’t be able to reply to the emails, which will be sent from no.reply@advice.hmrc.gsi.gov.uk.
In Conclusion
This VAT Return and Payment Overdue scam email has been timed to catch the unwary by being the right date, but a month early. Let people know that they should ignore the call to act immediately, and instead report the matter to IT security. Even if there is no malicious payload in the attachment, scam emails like this can disrupt the flow of energy in a business and ultimately cost money.
The Upside
On the upside, this scam is an early reminder that our VAT return has to completed at the end of this month, so I might go and give the finance team a gentle reminder!
Further Information
For authoritative information about when your VAT return is due, see www.gov.uk/vat-returns/deadlines
To report instances of this email scam, forward the suspicious emails to HMRC phishing team at: phishing@hmrc.gsi.gov.uk
