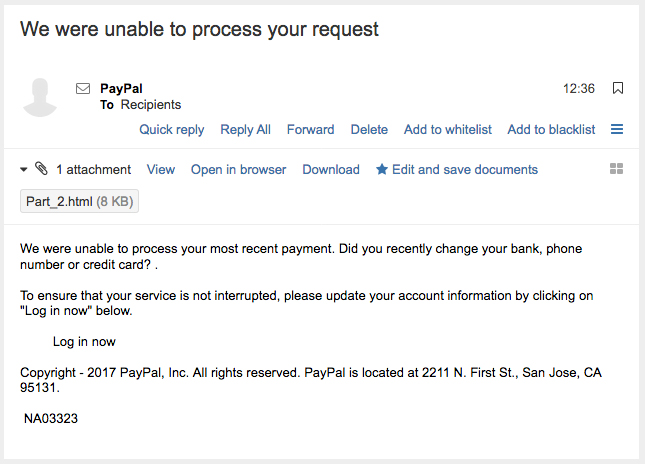
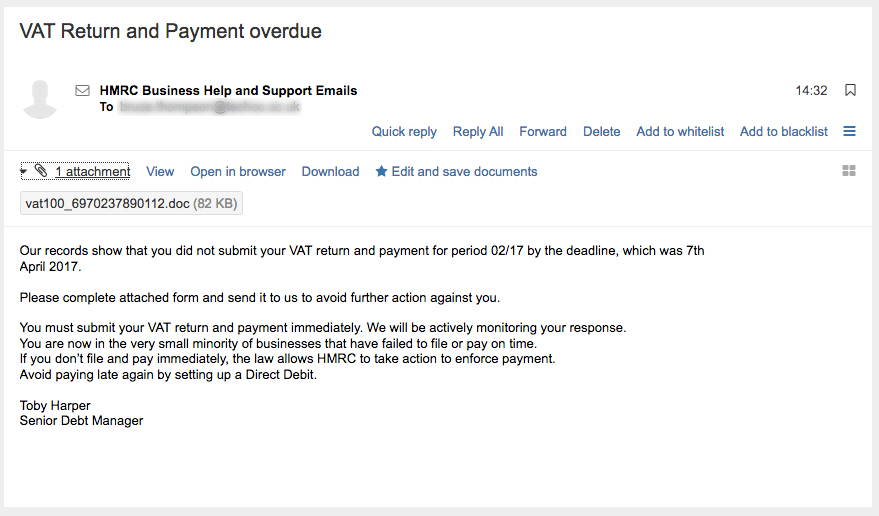
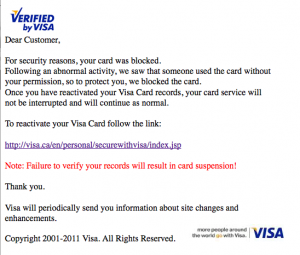
Have you seen reports about people from Microsoft Tech Support, who call you because you have malware on your computer? Have you had a call from a plausible sounding agency saying you have a virus on your PC? Did you feel uneasy about someone who knew your name and had details about how slow your PC was running? Chances are that you have been at least peripherally involved with a Phishing attack. Today’s security incident concerns the Microsoft Phone Scam, which is still running after eight years or so.
Why the Microsoft Phone Scam?
This attempt to get access to PCs, or personal information on them, often targets Windows users, so the scammer claims to be from Microsoft tech support. They target Windows based PCs, because there are a lot of them, but they are equal opportunity criminals. They will attempt to hack a Mac too.
What the Scammers Do
Today the support line received a call from a very helpful gentleman named Derek, who claimed to be from Microsoft tech support. He asked for me by name, which was nice, but then went on to explain how my PC had become infected by malware, and so was running slowly. A safe bet really. Is there anybody who doesn’t think their Facebook response time could be quicker? Pity that his technical report did not tell him I was using a Mac. Still, we decided to let the call run, as we were recording for training purposes.
He then proceed to explain that the fix for this problem was simple, and would only involve typing something into the command line. We got him to repeat the instructions several times to make sure we got it right. Had we actually been following his very patient instructions, we would have connected to fastsupport.com and accepted a GoTo Assist remote call. This would have given him unrestricted access to our PC, at user level, so he could have installed anything he liked.
Unfortunately we developed “technical difficulties” once we received the support key number, and had to hang up on Derek. He was persistent, and called back five times over the next ten minutes. He even let the phone ring for up to two minutes at a time. When we tired of this game, we answered, and informed Derek that we were cyber security specialists, investigating Phishing attacks. We told him that we were recording the conversation, and pointed out that our PC was, in fact, a Mac. He still tried to get us to accept the remote access call!
You couldn’t make this up!
How the scam works
Rather than producing computer virus directly, which is time consuming and involves skill, these scammers resort to Social Engineering. This is the practice of manipulating people so they give up confidential information. If they can trick you into letting them access your computer remotely, they can secretly install their malicious software themselves. That would give them access to your passwords and bank information, as well as giving them control over your computer.
How to deal with Microsoft phone scam calls
As Fast Support is a legitimate company, they have a mechanism to prevent abuse of their system. If you want to get one back at the scammers, play along up to the point that they give you the support key. Get them to repeat it a couple of times, to make sure you have it right, and then hang up and report the incident to Fast Support using the following link:
www.fastsupport.com/abuse. You will only need the support key number, and it only takes a couple of seconds
What Else You can Do
Probably the most important thing you can do is let people know about the Microsoft phone scam. It preys on people’s insecurity about their lack of technical knowledge. The best defence against Social Engineering is sharing knowledge, so tell everyone about it.
You can also report the incident to the police through www.actionfraud.police.uk/. As we have pointed out previously, they will only record the incident for statistical purposes.